- Get link
- X
- Other Apps
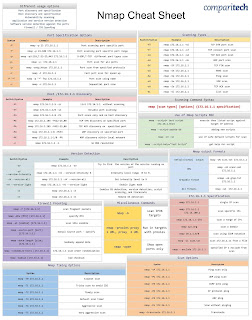
| 192.168.1.1 | |||
| IPv6 | AABB:CCDD::FF%eth0 | ||
| Hostname | www.target.tgt | ||
| IP range | 192.168.0-255.0-255 | ||
| CIDR block | 192.168.0.0/16 | ||
| file | -iL <filename> | ||
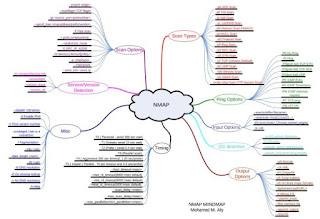
| Target Specification | #nmap [Scan Type] [Options] {targets} | ||
| Switch | Example | Description | |
| nmap 192.168.1.1 | Scan a single IP | ||
| nmap 192.168.1.1 192.168.2.1 | Scan specific IP's | ||
| nmap 192.168.1-254 | Scan a range of IP's | ||
| nmap scanme.nmap.org | Scan a domain | ||
| nmap 192.168.1.0/24 | Scan using CIDR notation | ||
| -iL | nmap -iL targets.txt | Scan target from a file | |
| -iR | nmap -iR 100 | Scan 100 random host | |
| --exclude | nmap --exclude 192.168.1.1 | Exclude listed host | |
| Scan Techniques | #nmap [Scan Type] [Options] {targets} | ||
| Switch | Example | Description | |
| -sS | nmap -sS 192.168.1.1 | TCP SYN port scan (Default) | |
| -sT | nmap -sT 192.168.1.1 | TCP connect port scan (Default without root privilege)(use sudo) | |
| -sU | nmap -sU 192.168.1.1 | UDP port scan | |
| -sA | nmap -sA 192.168.1.1 | TCP ACK port scan | |
| -sW | namp -sW 192.168.1.1 | TCP Window port scan | |
| -sM | nmap -sM 192.168.1.1 | TCP Maimon port scan | |
| Host Discovery | #nmap [Scan Type] [Options] {targets} | ||
| Switch | Example | Description | |
| -sL | nmap -sL 192.168.1-3 | No Scan. List targets only (only reverse-DNS lookup on the hosts) | |
| -sn | nmap -sn 192.168.1.1/24 | No Scan. Host discovery only. | |
| -Pn | nmap -Pn 192.168.1.1-30 | No host discovery. Only scan | |
| -PS | nmap -PS22-25,443 192.168.0.0/16 | TCP SYN discovery on port x (default port 80) | |
| -PA | nmap -PA21-30 192.168.1.0/24 | TCP ACK discovery on port x (default port 80) | |
| -PU | nmap -PU5-80 192.168.2.4-20 | TCP UDP discovery on port x (default port 80) | |
| -PR | nmap -PR1-443 192.168.1.0/22 | ARP discovery on local network only | |
| -n | nmap -n 192.168.1.1 | no DNS resolution | |
| Port Specification | #nmap [Scan Type] [Options] {targets} | ||
| Switch | Example | Description | |
| -p | nmap -p 21 192.168.1.1 | Port scan for port x | |
| -p | nmap -p 21-100 192.168.1.1 | Port range | |
| -p | nmap -p U:53,T:21-25,443 192.168.1.1 | Port scan multiple TCP and UDP ports | |
| -p- | nmap -p- 192.168.1.0/24 | Port scan all ports | |
| -p | nmap -p http,https 192.1.1.45 | Port scan from service name | |
| -F | nmap -F 192.168.1.1 | Fast scan (100 ports) | |
| --top-ports | nmap --top-ports 2000 192.168.1.1 | Port scan the top 2000 ports | |
| -p-65535 | nmap -p-65535 192.168.1.1 | Leaving off initial port in range makes the scan start at port 1 | |
| -p0- | nmap -p0- 192.168.1.1 | Leaving off end port in range makes the scan go through to port 65535 | |
| Service & Version Detection | #nmap [Scan Type] [Options] {targets} | ||
| Switch | Example | Description | |
| -sV | nmap -sV -p 43 192.168.7.6 | Attemps to determine the version of the service running on port | |
| -sV --version-intensity | nmap -sV --version-intensity 7 192.168.2.3 | Intensity level 0-9. Higher number increases possibility of correctness | |
| -sV --version-light | nmap -sV --version-light 10.2.3.5 | Enable light mode. Lower possibility of correctness. (Faster) | |
| -sV --version-all | nmap -sV --version-all 10.10.10.3 | Enable intensity level 9. Higher possibility of correctness. (Slower) | |
| -A | nmap -A 4.5.34.67 | Eables OS detection, version detection, script scanning and traceroute (NSE script) | |
| OS Detection | #nmap [Scan Type] [Options] {targets} | ||
| Switch | Example | Description | |
| -O | nmap -O 192.168.4.23 | Remote OS detection using tcp/ip stack fingerprinting | |
| -O --osscan-limit | nmap -O --osscan-limit 10.10.9.8 | If atleast one open and one closed TCP port are not found it will not try OS detection against host | |
| -O --osscan-guess | nmap -O --osscan-guess 10.10.9.8 | Makes Nmap guess more agressivlely | |
| -O --max-os-tries | nmap -O --max-os-tries 2 10.10.9.8 | Set the maximum number of OS detection tries against a target | |
| -A | nmap -A 4.5.34.67 | Eables OS detection, version detection, script scanning and traceroute (NSE script) | |
| FW/IDS evasion & Spoofing | #nmap [Scan Type] [Options] {targets} | ||
| Switch | Example | Description | |
| -f | nmap -f 10.10.10.9 | send packets fragmented | |
| --mtu | nmap -mtu 24 10.10.7.8 | set your own offset size | |
| -D | nmap -D 192.168.1.12,192.168.4.5,10.0.0.1 | Sends scan from spoofed IP's | |
| -D | nmap -D decoy1,decoy2 remote host | ||
| -S | nmap -S www.microsoft.com www.facebook.com | Scan Facebook from Microsoft (-e eth0 -Pn may be required) | |
| -g | nmap -g 53 192.168.5.8 | Use given source port number | |
| --proxies | nmap --proxies http://10.10.10.8:8080 | Relay connections through http/socket4 proxies\ | |
| --data-length | nmap --data-length 200 192.168.4.6 | appends random data to sent packets | |
| IDS evasion example | nmap -f -t 0 -n -Pn --data-length 200 -D 192.168.2.3,192.168.1.3 10.10.10.1 | ||
| NSE Scripts | #nmap [Scan Type] [Options] {targets} | ||
| Switch | Example | Description | |
| -sC | nmap -sC 192.168.1.1 | Scan with default NSE scripts. Considered useful for discovery and safe | |
| --script default | nmap --script default 192.168.1.1 | Scan with default NSE scripts | |
| --script | nmap --script=banner 192.168.1.1 | Scan with single script (ex. banner) | |
| --script | nmap --script=http* 192.168.1.1 | Scan with a wildcard (*) | |
| --script | nmap --script=http,banner 192.168.1.1 | Scan with two scripts | |
| --script | nmap --script"not intrusive" 192.168.1.2 | Scan default, but remove intrusive scripts | |
| --script-args | nmap --script snmp-sysdescr --script-args snmpcommunity=admin 192.168.1.1 | ||
| Output | #nmap [Scan Type] [Options] {targets} | ||
| Switch | Example | Description | |
| -oN | nmap 192.168.1.1 -oN normal.file | Normal output to the file normal.file | |
| -oX | nmap 192.168.1.1 -oX xml.file | XML output to the file xml.file | |
| -oG | nmap 192.168.1.1 -oG grep.file | grepable output to the file grep.file | |
| -oA | nmap 192.168.1.1 -oA results | output in the three major formats at once | |
| -0G - | nmap 192.168.1.1 -oG - | grepable output to screen -oN-,-oX -also usable |
- Get link
- X
- Other Apps
Comments
Post a Comment